Introduction to OSI Model
The Internet has made incredible growth in the last two decades. Now we are in the era of high-speed internet networks (yeah, still growing) supported by numerous satellites those rove around the planet. But as software engineers most crucial thing to us is to have a complete understanding of inter-host communication. Let’s try to recall what we learn in engineering and understand it with real-life examples.
OSI Model stands for Open System Interconnection. The reference model describes how information from one computer’s application transfers through a physical medium to the application in another computer. In 1984 OSI model was published by ISO(Internation Organization for Standardisation ) as standard ISO 7498, and the renamed CCITT (now called the Telecommunications Standardization Sector of the International Telecommunication Union or ITU-T) as standard X.200. it is considered an architectural model for inter-computer communications.
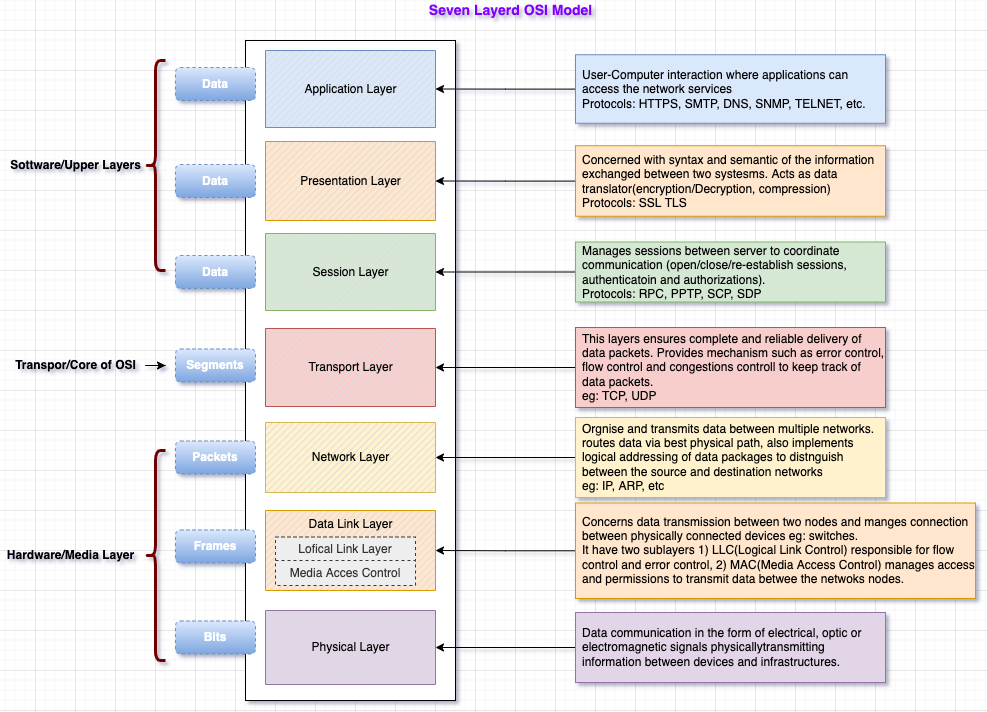
OSI consists of seven layers, and in each layer, a set of particular network functions get performed.
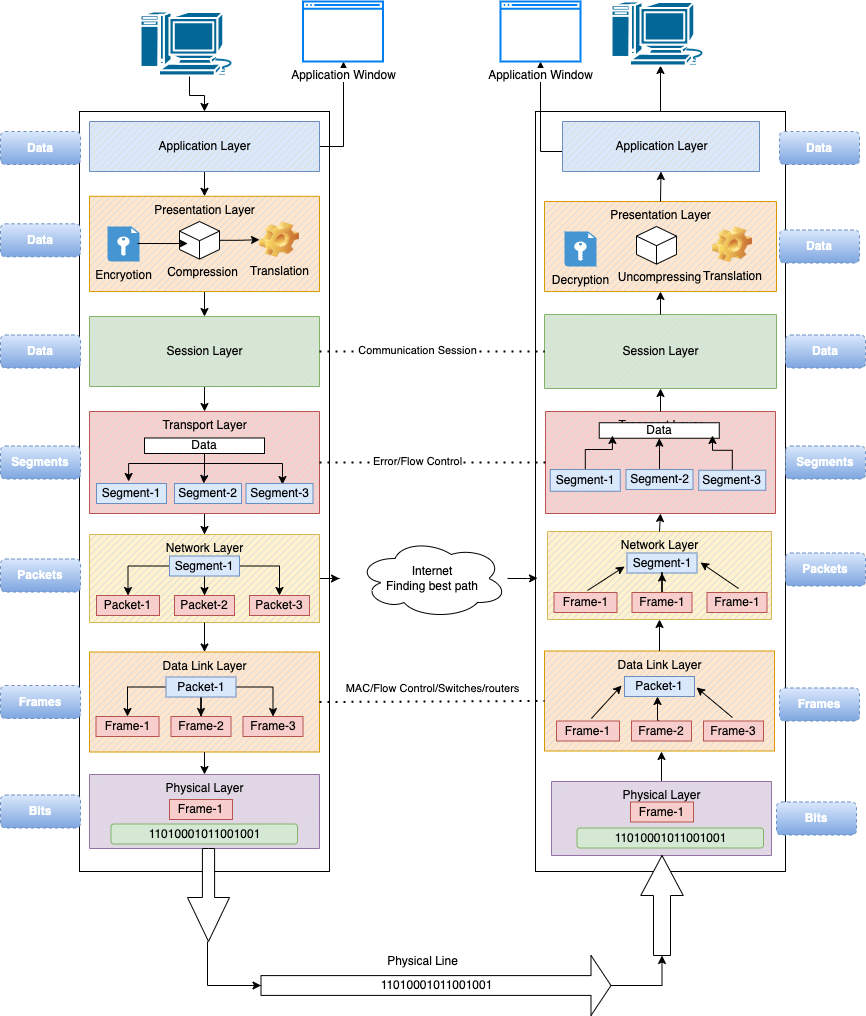
There are plenty of resources available over the Internet to read about each layer’s OSI model functions and responsibilities. I have tried to accommodate my reading in the following diagram. Let’s look at that, and I will try to explain the OSI model with a real-life example.
For example, Aryan wants to send an email to Arjun.
What Happens at Aryan’s end.
Aryan opens an email application on his laptop, composes a message, and hits a send button. His email application will pass the message to “Application Layer,” which will pick protocol SMTP(Simple Mail Transfer Protocol) and pass the data along to the “Presentation layer.” The presentation layer will do the job of data compression and encryption. Once data is prepared and ready for communication, the “Session layer” will come into the picture, initializing the communication session; it could be either half-duplex or full-duplex. In the session layer, some checkpoints get added while transmitting the data in sequence. If some error occurs in the middle of data transmission, the transmission will resume again from the checkpoints.
Then data will hit the “Trasport layer,” where it will be segmented and ensured that messages are transmitted in the order they sent, and there is no data duplication. The transport layer takes care of flow control, sending data at a rate that matches the connection speed of the receiving device and error control. Here it uses protocol TCP where the connection between host established. Then Network layer takes the next job of breaking down segments into network packets and finding the best network path for transmission.
The data link layer establishes and terminates a connection between two physically-connected nodes on a network. It breaks up packets into frames and sends them from source to destination. This layer comprises two parts—Logical Link Control (LLC), which identifies network protocols, performs error checking, and synchronizes frames. Media Access Control (MAC) uses MAC addresses to connect devices and define permissions to transmit and receive data.
Now data comes to the physical layer, which includes the physical equipment involved in the data transfer, such as the cables and switches. And in this layer, the data will get converted into a bitstream of 1s and 0s.
Now data stream of 1/0 has been reached to Arjun computer after all seven layers processing and passing through the physical medium.
The data will flow through the same series of layers on his device but in the opposite order. The physical layer will convert bitstream(0s and 1s) to frames and pass them to the data link layer. The data link layer will reassemble frames into packets for the network layer. The network layer will then make segments out of the packets for the transport layer, reassemble the segments into one piece of data. The data will then flow into the session layer, which will pass the data along to the presentation layer, and then end the communication session will get completed. The presentation layer will then uncompress data and decrypt it before passing it to the application layer. Now the application layer will feed data to Arjun’s computer email software to read the email.